The internet is so awesome, man! We use it all the time for such things as chatting or stalking people’s social media pages. Beware of it though! The Internet is like a forest full of hidden hazards waiting to strike at any time! These dangers are similar to villains who steal our information, damage our phones, and make the internet a bore!
Phishing Scam
Imagine receiving an
email from your bank saying “BIG PROBLEM WITH YOUR ACCOUNT!” It might even have
some fancy logo and colors so that it would look real. This is called a phishing
scam! They want you to click a bad link or give them your secret password or
credit card number! Such links lead to fake sites where personal details are
stolen from you, or malware is downloaded onto your gadget. Phishing emails are
like deceitful companies that appear trustworthy!
Malware
Malware, an abbreviation for
malicious software, functions just like a mean guest who has checked into your
computer or phone. Just as there are different categories of hooligans, so can
malware be classified in various ways! Viruses are like colds that one gets
from friends and tend to spread from one device to the other. On the
other hand, worms keep on duplicating themselves like those irritating salespeople who never let go of you! Yet Trojan horses mimic something good only for
it to destroy information or mess up your device after you have downloaded it.
Nevertheless, such programs inevitably bring malware to your PC by clicking bad
links, opening weird e-mail attachments, and more.
Data breach
Imagine someone breaking
into locked cupboards and stealing all your vital documents! Data breaches are
like that, but as opposed to bins we've personal facts like passwords and
credit card statistics. Hackers, negative safety, and mistakes also can result
in those breaches. If your facts are stolen, they can be used for
nefarious purposes like stealing your money or cyber harassment. Yikes!
But wait! Here is the solution!
Amid the thriving virtual
platform, where the risk to cybersecurity rises to great heights, SquareX has
come up, with modern approaches to assure online safety. The most outstanding
feature of their product line is the cornerstone of browser extensions and
cloud devices that work efficiently to deter online sneaking and protect
digital identity.
The extension of SquareX
acts as a perfect shield against online hazards in a myriad of types
forming a security umbrella by protecting against sites with malware and
phishing attempts. In contrast to traditional security products that control
file access quite frequently, SquareX provides the ability to view
securely, open, and work with files and platform applications within a sandbox.
The empowering article, an exciting enhancement to the browser environment, has
received huge support from people who admire its efficiency in ensuring
that internet security and privacy are pushed to the next level.
This article gives information about how SquareX is useful to fill up the gaps in online security and privacies through the practice of such without any promotional or advertisement of a certain product or service. It can either be a playground or a battlefield and it all depends on the person's knowledge and expertise on information technology.
Among the features that
SquareX is proud of is its ability to insulate online actions from malware and
vuln areas, guaranteeing the safety of its users during the time they spend protecting
themselves within its secure premises. However, it is not only bound to the
extension but covers a range of advanced technologies and services addressing
both people's and businesses' privacy protection needs. A combination of encryption
and access control mechanisms come embedded in these solutions and cater to an
all-in-1 approach to online security.
Being distinguished and emboldened by top professionals and participants in the tech world, SquareX has so far set a firm place in the digital universe. It has been SquareX’s principal personality either a pillar of defense for all enterprising businesses or a provider of an impeccably innovative online experience that places itself at the forefront of internet security.
Potential Benefits, Considerations, and Limitations
SquareX provides innovative means of security and privacy for online files, web browsers, and email through its main features, namely, file viewing, browser, and email for temporary content, for temporary use. Here's a detailed look at the potential benefits of each:
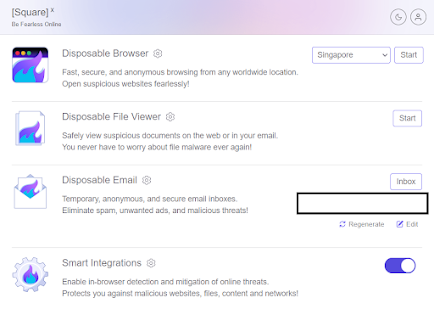
1. Disposable File Viewing:
SquareX: conversely, the existence of disposable file viewing is an absolute
novelty. These files are secure and confidential when opening files online.
This smart ability of users allows them to sort files in the cloud warehouse.
What they see is only the image of the sandbox in which the actual files will
be opened and processed. This isolated environment embeds users against
all potential threats, which are hidden within the files, like a window to an
intruder infected with malware or a virus. Also, note that since these files are
temporary they don't allow files to be permanently stored on the temp
devices minimizing the risk of data breaches or unauthorized access.
2. Disposable Browser: The point-and-click
browser by the company named SquareX is an embodiment of power that is aimed to
keep users anonymous and untraceable as they are connected to the World Wide Web. Private environment isolation along with the disposable browser enables
users to have all their online activities remain undetected and secure with no
possibility of getting compromised. The private browsing feature will let them
access any website that will not be kept anywhere and won't be tracked or
stored. This mode is really helpful to those people who give priority to
their personal data protection and avoid situations when third-party tracking
companies gather data about their online actions.
3. Disposable Email:
SquareX's approach to single-use email as an extra protective cover for users
who communicate online brings forward all-around privacy and security. This
way they have an opportunity to create temporary email addresses and use them
for specific tasks, like for signing up some service on the web or just
chatting with strangers. With this done, users could, without any
hesitation, dispose of the email address piling up in their inboxes. This would
help in expelling the spam and phishing emails. Users can create a temporary
and disposable email address for situations where they do not want to share
their personal email with a third party. This ensures the users' full control
and minimizes the risks associated with identity theft or email-based attacks.
Limitations
1. Storage Constraints: A situation where a user can temporarily view a file can come in the way of storage capacity available for memory access. Users with a large number of file management tasks may encounter problems such as space restriction of documents and difficulty in viewing or enjoying them.2. Offline Access: According to SquareX the disposable function needs to be connected to the internet. Online storage defeats the purpose of offline, so you may not be able to access files, browsing sessions, and e-mail, which would most certainly limit productivity in some cases.
3. Dependency on Third-party Services: The incorporation of cloud computing and externally hired service providers provides the base for the functional expertise of SquareX. User's concept of independence and security may be undermined as they rely on external services; however, this should not compromise one's awareness of the impact of such dependencies.
Finally, SqareX can provide a large number of advantages, such as a higher security level, privacy protection, and the ability to stay anonymous online. On the other hand, users need to be cautious regarding factors like simplicity of operation, compatibility with other platforms, and existing restrictions when they are implementing SquareX into their day-to-day digital work.