AI is one trend among many to mark the ever-changing cybersecurity landscape, as it can be used both by attackers and defenders. The AI can improve productivity through automating repetitive tasks and strengthening the analysis, but, at the same time, it can be a possibility of cyber threats, if it is in the wrong hands.
Through this article, we are demonstrating the
AI tool analogous to ChatGPT, which has been created only for ethical
hacking and penetration testing purposes. Here, we will explore the positive and negative sides of such a technology in a moderately applicable way.
Questions Covered-
What are the key applications of the private
GPT tool in cybersecurity?
How can the private GPT tool assist in vulnerability
identification?
The Benefits of An Uncensored AI Tool to Recognize Ethical Hacking
§ Automated Vulnerability Discovery: AI could scan code, network settings, and system parameters which could lead to much faster vulnerability detection and help to prevent issues before they occur.§ Social Engineering Simulations: The generator could produce phishing emails, social media posts, and other kinds of social engineering attacks which are usually for the victimizing of companies.
§ Exploit Code Generation: Although an ethical dilemma, the one with the capacity to create basic exploit code will definitely enhance knowledge and patch vulnerability in a manner that does not require manual approaches.
Benefits and Considerations:
§ Risk of Malicious Use: The prospect of an individual having unfettered access to this type of power can seriously jeopardize the world. Ethical principles and robust security systems would be needed to oversee the technology and ensure that it wouldn’t be abused.
§ Legal and Regulatory Concerns: In the case of an exploit code creation which is done not only for research purposes but also for commercial purposes, it could cause problems in the law. The necessity of seeking the opinion of legal experts should never be undermined.
§ False Positives and Negatives: AI models are not necessarily perfect. This tool may produce false alarms (which are nicknames for conditions where the vulnerabilities do not exist) and failures (no critical vulnerabilities are detected). Integration of human experts for authentication still remains an important issue.
Like SquareX, NordVPN's antivirus feature offers complete coverage of your online security and privacy considerations, too. Thus, it makes sense to make use of these types of virus protection apps. Users now have access to a bundle of features that make up the line of antivirus products created by Nord. All these features are carefully designed to secure against all types of cyber threats, protecting users’ data privacy, at the same time. By grasping the latest technology along with a user-oriented interface, the antivirus of NordVPN perfectly cares for the digital life of its customers and provides them the level of trust they need to confidently surf the Internet. Embrace the tranquility of being certain that your computer has been protected against malware, viruses, and other malicious code, so you can detect and respond to potential dangers sooner and provide a safer computing environment. Start on the path of better online security and privacy by using the antivirus software provided by NordVPN.
Questions Covered-
How can
users incorporate the private GPT tool into their cybersecurity workflows to
enhance security practices?
Installation and Setup
Definition and Purpose of Ollama
To implement and manage our private GPT, we shall turn to Ollama, which is a multi-purposed backend manager designed to simplify the deployment and use of open-source language models. Ollama plays a cardinal role in taking care of and administering LLMs. It is a bridge between models and users, letting them communicate successfully via CLI for model management and deployment. Through Ollama, users will be able to design, run, and tailor language models depending on the usage and task.
Downloading and Installing Ollama
1. Visit the Official Ollama Website: The Ollama website is the direct link to the platform's official site where the recent version can be downloaded.
2. Download Ollama Installer for Windows: After selecting your computer type, download the installer.
3. Run the Installer: After the download is finished, find the installer (for instance `OllamaSetup.exe`) in the location where it has been downloaded and double-click it to start the installation.
4. Follow On-Screen Instructions: The installer will walk you through the installation process and the wizard will actually show you how to do it. Do the task by selecting the option that is suitable and correctly answering the prompts.
5. Complete Installation: The Windows installation for Ollama will be ready for use.
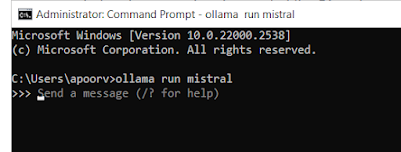
Starting Ollama Service
1. Open Command Prompt: click on `Win + R`, type `cmd`, and hit Enter to bring up a Command Prompt window.
2 Pull model and run Ollama Service: Use this command to begin the Ollama service:
ollama run [model_name]
For
eg. llama2 or mistral
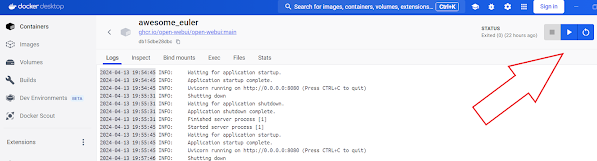
Installing Open Web UI
1. Ensure Docker Installation: If not already installed, download and install Docker Desktop for Windows from the official website.
2. Build Docker Image and Run Docker Container:
docker run -d -p 3000:8080 --add-host=host.docker.internal:host-gateway -v open-webui:/app/backend/data --name open-webui --restart always ghcr.io/open-webui/open-webui:main
Running
Your Own Private GPT
With Ollama and Open Web UI set up, you can
now access your own private GPT tool through the web interface. Open your web
browser and navigate to http://localhost:3000 to start using the tool. You can
interact with the GPT model, store prompts, and manage your chats seamlessly.
Navigating the User Interface
First-time Setup: An Initial setup as
follows: users’ accounts creation, administration module, permissions, and
access control.
Account Creation:
· First of all, visit AI's platform or app (using
http://localhost:3000).
· Go for the widget that shows “Sign up”.
· Complete the mandatory information like user
name, email, and password.
· After creating an account, log in using your
credentials.
· Explore the dashboard or settings section to
access administrative functions.
Questions Covered-
In what ways does the private GPT tool aid in
exploit development?
What functionalities does the private GPT tool
offer for password cracking and security audits?
How does the private GPT tool contribute to
analyzing network traffic and threat intelligence?
What are the potential benefits of leveraging
the private GPT tool in addressing cybersecurity challenges?
How does the private GPT tool empower
cybersecurity professionals to stay ahead of emerging threats?
What role does AI-powered technology play in
bolstering cybersecurity defenses?
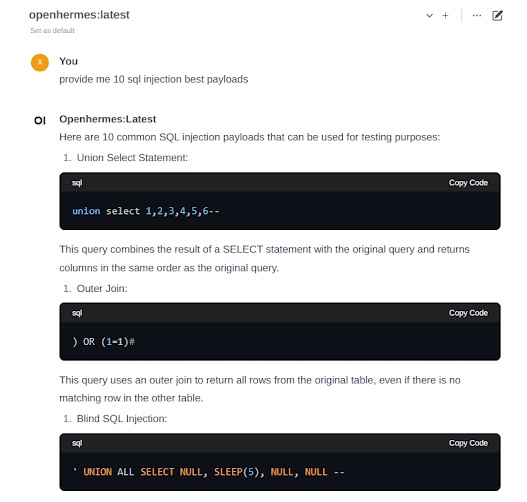
To show that the private version is capable of the same thing, I have
tested some prompts related to cybersecurity. Following that we will share
visuals (i.e. screenshots) of the prompts we used and the corresponding AI
model’s replies concerning cybersecurity.
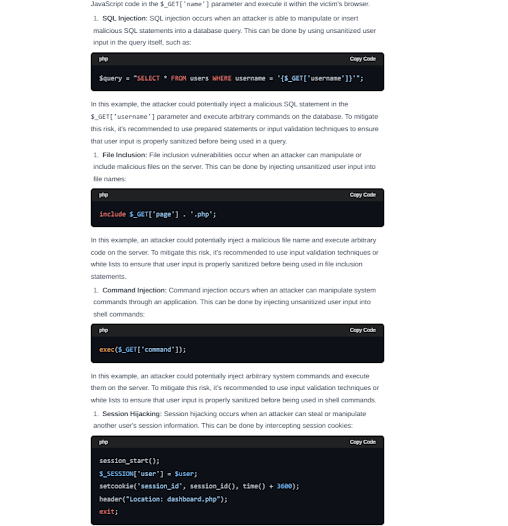
Next, we provided a part of the vulnerable code from DVWA and checked for the raised vulns.
In
a nutshell, the demo of the privately developed GPT in cybersecurity
illustrates the importance of having it in the cybersecurity practitioner's toolset. AI-powered
capabilities of the tool help users eliminate the hassles of multiple tasks,
including scanning for vulnerabilities, generating exploits, and cracking passwords.
The screenshots and prompts featured in our experiments reveal that the GPT
shows great talent in helping cybersecurity learners get valuable information
and directions on any domain in the cybersecurity area. Whether for
network traffic analysis, finding security defects, or creating attack code,
this tool is very versatile, and it is like having a friend for security
personnel.
In addition to this, the availability and ease of use that the private GPT tool
provides serve as a means to reach both expert cybersecurity professionals and
beginners in cybersecurity. Its straightforward user
interface and the contextual relevancy of its responses empower users to make
quick decisions and lead to the discovery of security gaps within their
organization.
In the present era of ever-changing threats, entities that possess the latest technology such as the one can achieve a superior position in cybersecurity practices and proactively defend themselves against
adversaries. Alongside our search for AI-driven tech in cybersecurity GPT
helps to meet the complex security challenges faced across the globe.
If
it’s so you’ve found this blog helpful and insightful, look for our other
articles covering the topic of online security and privacy. Besides, make sure
to visit my YouTube channel for
more updates on cybersecurity and technology trends. You can also engage me
often on different social media platforms for regular posts and discussions.
Thank you for your immeasurable support and participation.